Our network is capable of absorbing all attacks. We can provide more than 200Gbps of active in-line filtering for comprehensive protection. Additionally, for large-scale attacks, we leverage the support of our upstream providers, who contribute with a mitigation capacity of 4+ Tbps for volumetric attacks, our network is able to withstand and mitigate a virtually unlimited number of attacks. Through this robust infrastructure, we ensure uninterrupted service delivery while guaranteeing all our customers' SLAs.
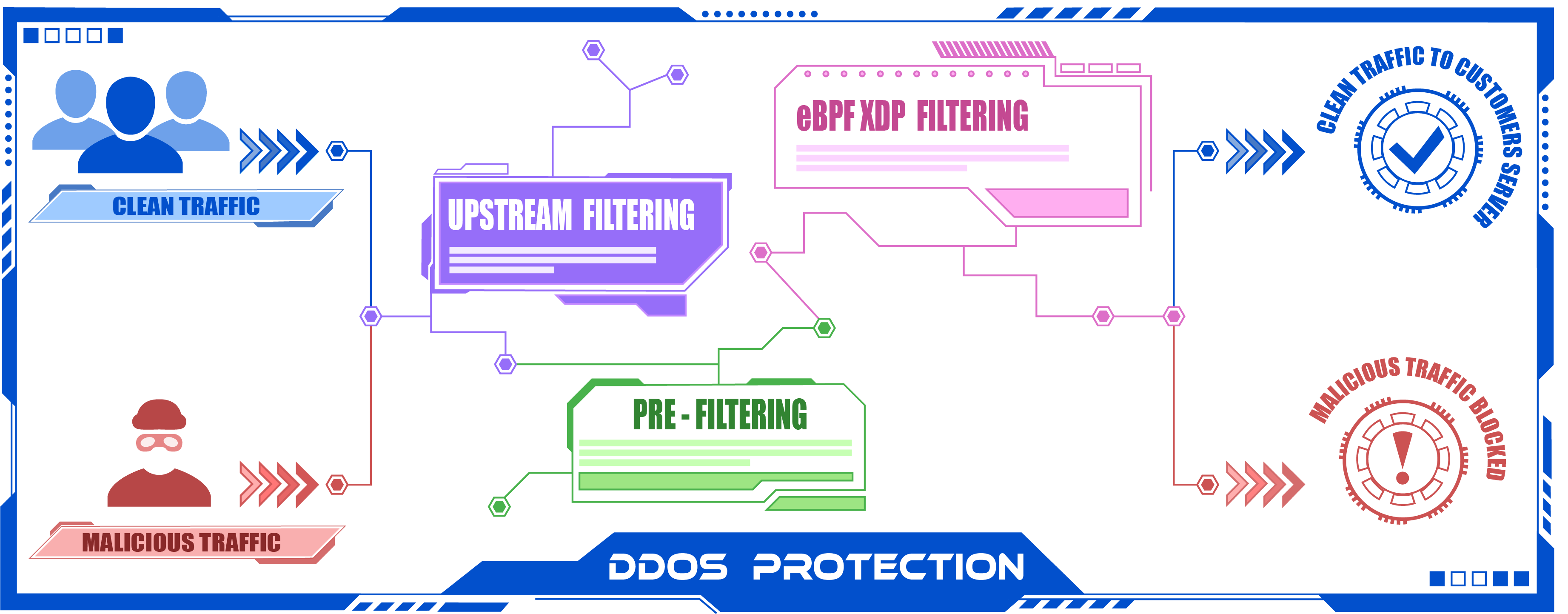
To protect your servers and services from attacks, we offers a mitigation solution based on multiple combination of techniques:
Traffic analyze and attack detection
We use the sflow sent by the routers and analyzed by our sensors to identify attacks. Each router sends a summary of traffic in real time. Our sensors analyzes this summary and compares it to the attack signatures and thresholds. If the comparison is positive, the mitigation is set up instantly.
Understanding DDoS
In today's interconnected world, distributed denial of service (DDoS) attacks pose a significant threat to businesses of all sizes and across all industries. These attacks aim to disrupt and disable servers, services, and entire infrastructures by overwhelming them with an enormous volume of traffic or by exploiting their resources until they are exhausted.
During a DDoS attack, a multitude of requests is simultaneously generated from various sources across the internet. This orchestrated 'crossfire' of traffic overwhelms the targeted system, causing it to become unstable or completely unavailable. The attackers may employ various techniques to amplify the impact of their assault, such as botnets, which are networks of compromised devices that can be controlled remotely.
The consequences of a successful DDoS attack can be severe for businesses. They may experience significant financial losses due to downtime, loss of productivity, and potential damage to their reputation. Additionally, the attack may also serve as a diversionary tactic, aiming to distract IT teams while other malicious activities, such as data breaches, occur simultaneously.
More Questions?
We are delighted to address any inquiries you may have. Feel free to reach out to us via email at info@lowhosting.org or by using our Contact Us form.
